As OT protocols often lack security features, it means valuable data is more likely to be subjected to a sniffing attack.
- Encrypt critical data such as configurations
- Deploy secure remote access


Driven by both top-down and bottom-up forces, industrial cybersecurity has become an urgent initiative in many different industries. On one hand, the growing number of cybersecurity incidents and cyberattacks on critical public infrastructure, such as power substations, oil and gas pipelines, and water treatment plants, has prompted governments around the world to implement new laws and regulations that demand stronger industrial network security.
On the other hand, private companies and smart factories are also realizing that they are no longer immune to cyberattacks and are also taking matters into their own hands to address potential cybersecurity risks on their networks. Indeed, industrial cybersecurity has become everyone’s responsibility and demands a new way of thinking.
Download Moxa’s case studies to see how their solution helps to strengthen your industrial network security at every step of the way.
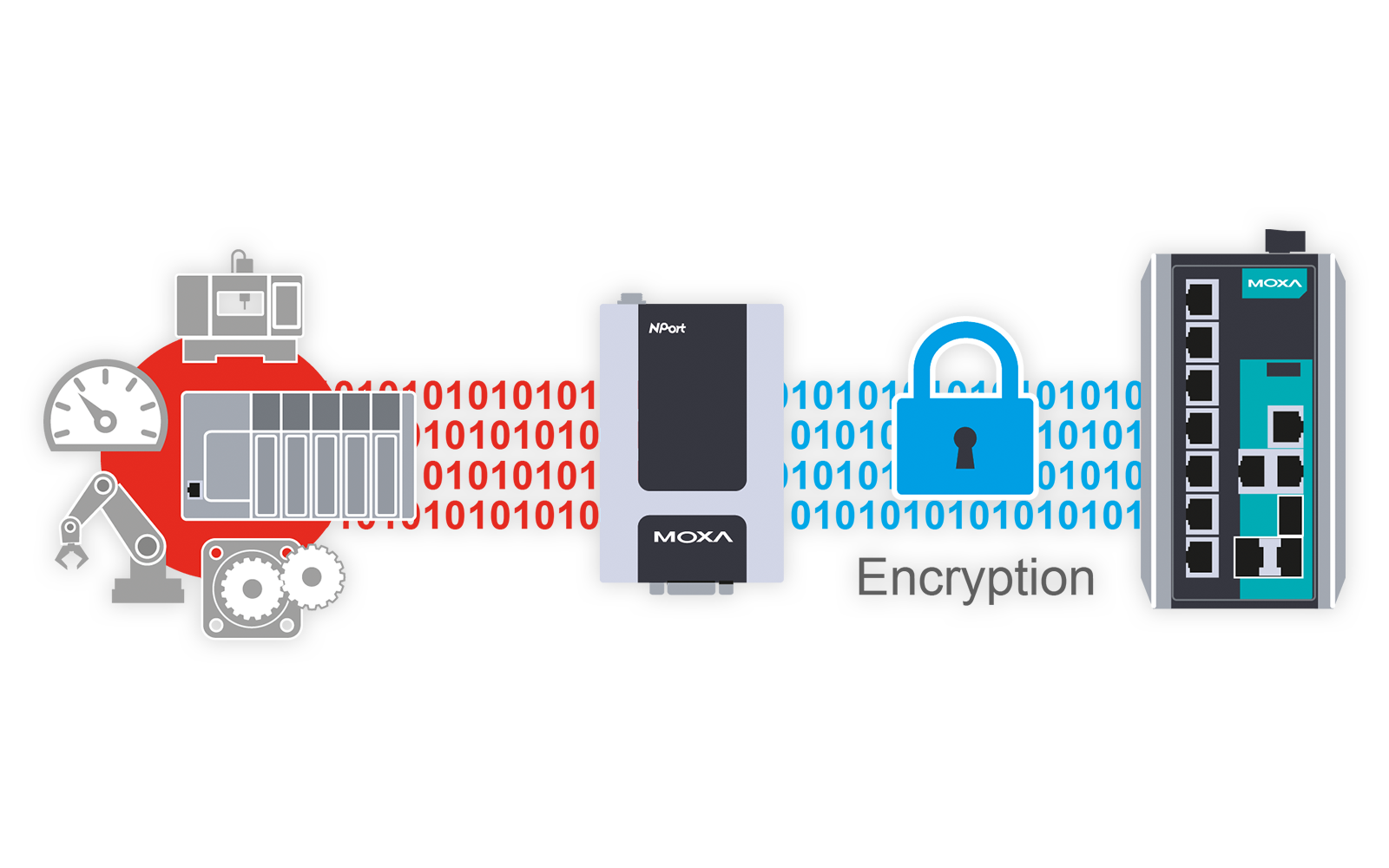
As OT protocols often lack security features, it means valuable data is more likely to be subjected to a sniffing attack.

As more and more devices are connected, it is imperative to control access to your networks and devices.
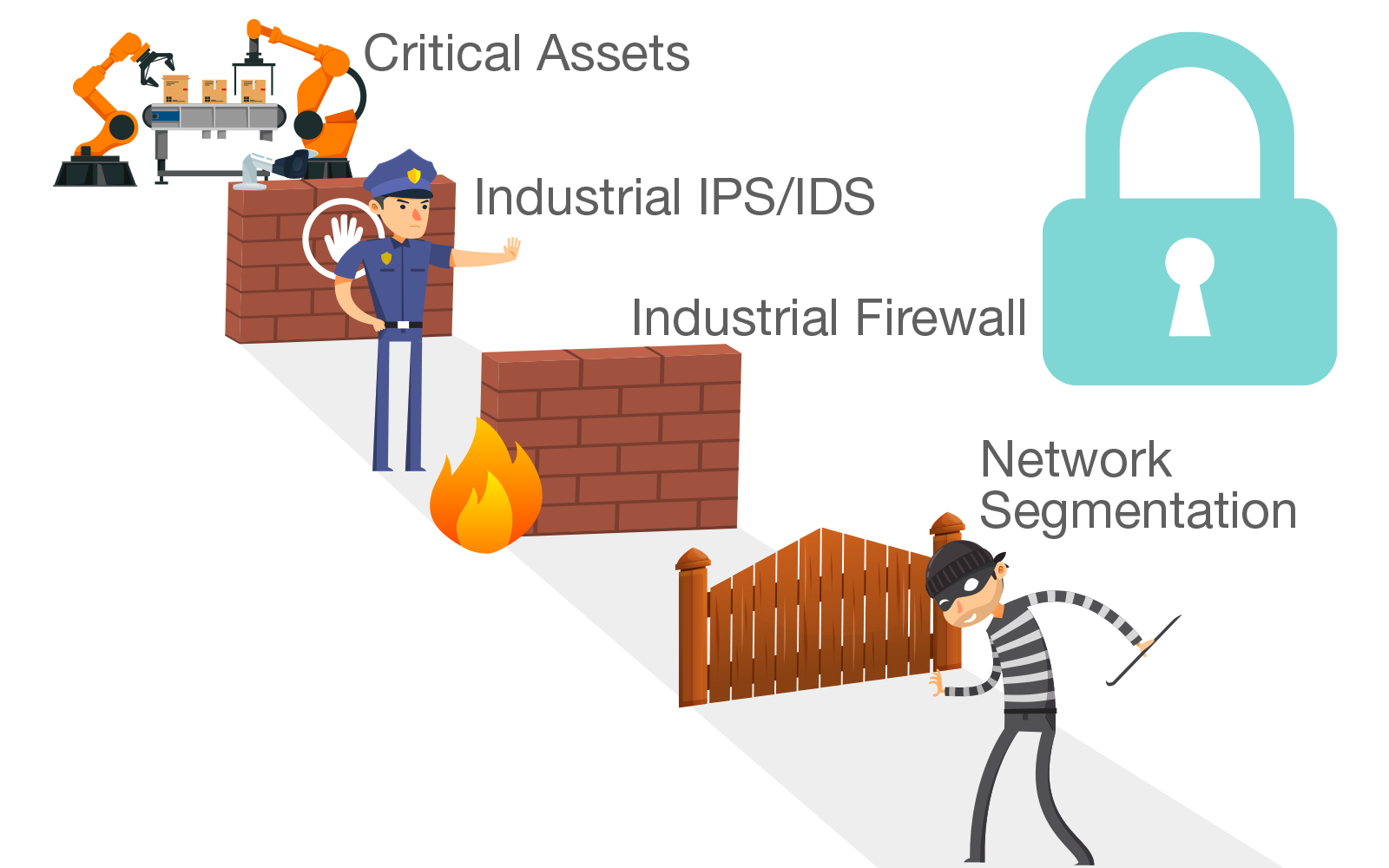
Flat networks are commonplace in OT environments, which has allowed cyberattacks to spread across entire networks in recent years.
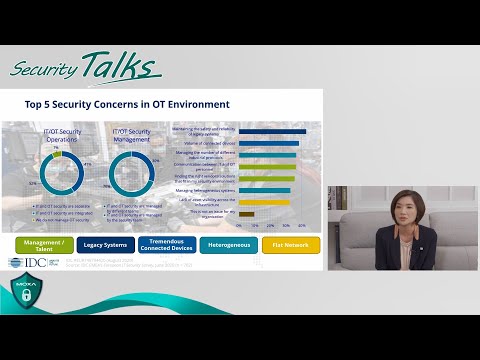
More than 30% of respondents to IDC EMEA’s European IT Security Survey in 2020 thought that a lack of asset visibility across network infrastructure was a security concern.

More than 40% of respondents to IDC EMEA’s European IT Security Survey in 2020 thought there were security concerns regarding maintaining the safety and reliability of legacy systems.
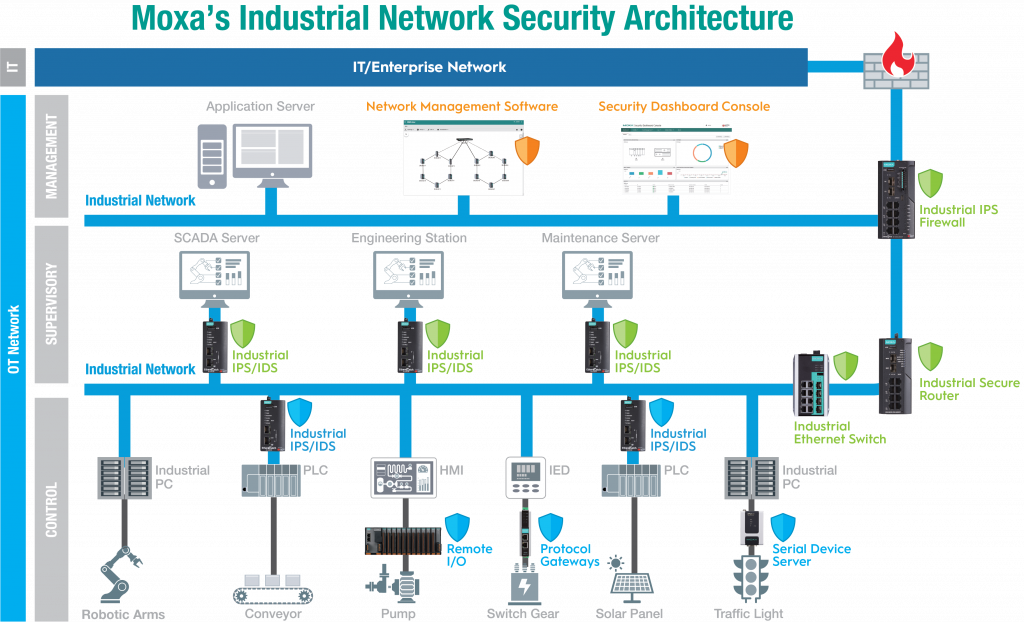
With an ongoing commitment to ensuring reliable connectivity for industrial environments, Moxa has enhanced its network security portfolio with Industrial Cybersecurity Solution to mitigate cyberthreats against industrial networks. Download the solution flyer to learn more.
Moxa has invited industry experts to discuss how to protect industrial networks. If you are interested in learning about their insights
don’t miss these Security Talks videos.


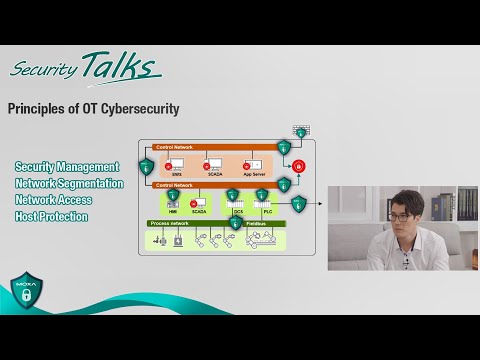

To close the gap between the OT and IT worlds, Moxa offers coordinated solutions that are
designed to completely protect your industrial networks.

Moxa unites industrial networking and cybersecurity expertise to provide layered protection for your industrial networks.

Moxa takes a proactive approach to protect our products from security vulnerabilities and help our customers better manage security risks.
Moxa has partnered with TXOne Networks to respond to the growing security needs of industries as well as the security demands from IT/OT personnel.