
The Fundamentals to Industrial Cybersecurity
Effective cybersecurity management is imperative for all organizations. There are many standards and guidelines available for organizations to refer to in order to move forward. In this article, we will introduce specific action items based on well-defined frameworks and standards when building a cybersecurity management system for your own ICS (industrial control system). Taking a defense-in-depth approach to network construction and choosing secure-by-design solutions from trusted vendors can help simplify the ICS cybersecurity decision-making process.
Key Elements of the Cybersecurity Management System
In order to understand the key elements of the cybersecurity management system (CSMS), we can take an in depth look at one of the well-defined industry standards, the IEC 62443 series of standards, which provide a holistic and wide-ranging approach to securing industrial control systems (ICS). Although these standards provide a wealth of information to asset owners, supply chain managers, and product development teams in an ever-expanding spectrum of field applications, it can be difficult to distill concrete action items for building your own ICS cybersecurity management system. Here, we identify the main elements in the CSMS development process proposed by the IEC 62443 standards.
Key Elements Proposed By The IEC 62443 Standards
- Initiate a CSMS program
- High-level risk assessment
- Detailed risk assessment
- Establish security policies, organisation, and awareness
- Select and implement countermeasures
- Maintain the CSMS
Action Items Implied
Provide information that is required to get support from management
Identify and assess the priority of risks
Conduct detailed technical assessment of vulnerabilities
Establish security policies, relevant organisations, and awareness among employees
Reduce risks to the organisation
Ensure the CSMS remains effective and supports the organization’s goals
Asset owners, system integrators, and product suppliers play key roles in the whole cybersecurity management system as suggested in the IEC 62443 standard (Figure 1). In particular, the IEC 62443 standard recommends that asset owners analyze, address, monitor, and improve the cybersecurity management system’s ability to defend itself against risks in accordance with the company’s risk appetite. In addition, the IEC 62443 standard recommends security development throughout the product lifecycle to maintain an acceptable level of security in the products and systems the solution providers or system integrators offer.
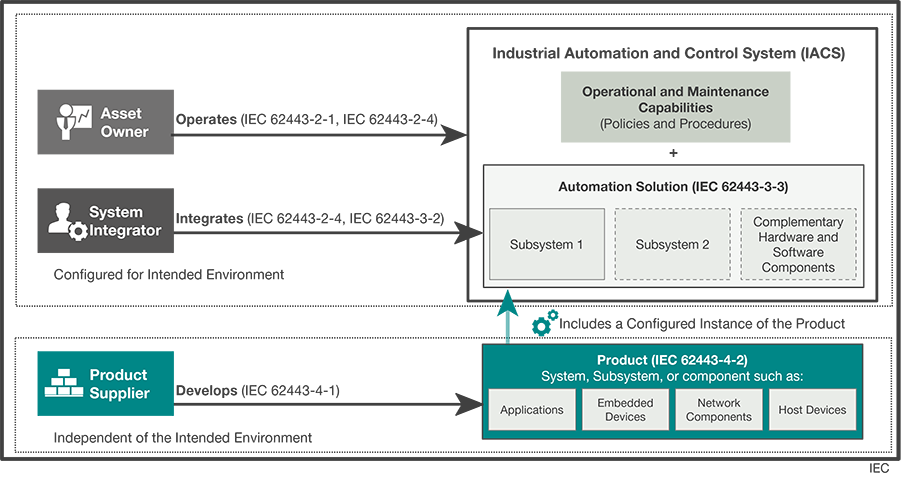
There are two principles mentioned in the framework above that encourage you to take the following concrete actions:
- Taking a defense-in-depth approach to network construction.
- Choosing vendors that provide secure-by-design solutions, which include after-sales service and established security response processes.
Following these two principles will help you protect your devices from security vulnerabilities and help you to manage security risks better.
Build Defense-in-depth Networks
One of the most common security weaknesses in an ICS is the use of flat networks that allow all the devices on a network to communicate with each other, even if it is not necessary. A flat network architecture contributes to a lack of control over information on the network and facilitates both threat propagation and communication degradation.
Taking a page out of the military playbook, asset owners can adopt the defense-in-depth approach when building their network. In the military context, defense-in-depth refers to implementing multiple levels or layers of protection to prevent an intruder from advancing. Similarly, defense-in-depth networks are partitioned into multiple zones and conduits, which are each assigned different security levels depending on associated risks.
Assess Security Levels
An important part of the defense-in-depth strategy is to consider countermeasures for zones and internal products. Accordingly, the IEC 62443 standard introduces the concept of security levels that can be applied to zones, conduits, channels, and products. The security level (SL) is defined by researching a particular device, and then determining what level of security it should have, depending on its place in the system. The security levels may be classified into four distinct levels 1 to 4, (although the standard also mentions an “open” level 0 that is rarely used):
- Security level 1 (SL1) is a casual exposure.
- Security level 2 (SL2) is an intentional attack with low resources.
- Security level 3 (SL3) is an intentional attack with moderate resources.
- Security level 4 (SL4) is an intentional attack with extensive resources.
Balance Risks and Costs
Once the required SL of a zone is defined, it is necessary to analyze if the devices inside the zone can meet the corresponding security level. If they do not, it is necessary to plan which countermeasures can help reach the required SL. These countermeasures can be technical (for example, a firewall), administrative (that is, policies and procedures), or physical (for instance, locked doors).
It is important to note that not every zone, conduit, or device requires Level 4 security. Asset owners or system integrators need to conduct a detailed risk analysis to determine the appropriate level of risk for each zone and conduit in their system. In other words, there is an inherent balancing of risk and cost that asset owners and system integrators need to consider.
Choose Hardened Components
The concept of security levels also applies to the components that go into building the system. In fact, the IEC 62443-4-2 standard specifically defines the security requirements for four types of components:
- Software applications
- Embedded devices
- Host devices
- Network devices
For each type of component, the IEC 62443-4-2 standard also defines seven foundational requirements:
- Identification and authentication control
- Use control
- System integrity
- Data confidentiality
- Restricted data flow
- Timely response to events
- Resource availability
Luckily, there are several laboratories, such as Bureau Veritas and ISA Secure, that can certify products to ensure they adhere to IEC 62443-4-2 requirements. These laboratories can simplify the selection process for asset owners. All you need to do is determine the level of security required and select a certified product that meets that requirement.
This component level security assurance, also known as hardening, adds another layer of protection to the system as part of a defense-in-depth strategy.
Select Secure-by-design Suppliers With After-sales Support
Besides selecting security hardened devices, asset owners also need to pay careful attention to supply chain management practices. In fact, after-sales support and response to vulnerabilities are just as important as how the devices are designed and built. That’s because the components that go into building a cybersecurity management system often come from separate vendors. If a vendor’s devices are compromised, then the devices and potentially your entire system could be too. So, besides device level security, you will also want to choose suppliers that provide security throughout the entire product lifecycle, including support, quality control, validation of performance, and vulnerability responses, among other aspects.
In other words, the entire product lifecycle needs to be secure-by-design. The IEC 62443 standard has even dedicated a specific subsection, IEC 62443-4-1, to specify the requirements for ensuring ‘secure-by-design’ throughout the product lifecycle (that is, building, maintaining, and discontinuing devices). These requirements are generally associated with the support needed for patch management, policies, procedures, and security communications about known vulnerabilities. Similar to the IEC 62443-4-2 standard for product certification, it is possible to certify that a solution provider is following good security management practices and adheres to tangible criteria in the IEC 62443-4-1 standard simplifying the asset owner’s decision-making process.
