From a management point of view, OT engineers need to know the network status, as it can indicate if there are uncontrolled network paths through which attackers can access the system, and to review network devices to ensure they are well prepared against unwanted people accessing and attacking devices. Managing a network is not an easy task. An OT NMS tool with comprehensive visibility could benefit OT engineers by managing and securing OT networks in different aspects.

Network Visibility is Critical for OT Cybersecurity
Nowadays, there are more and more operational technology (OT) devices connected by Ethernet infrastructure. As industrial IoT technologies (IIoT) and Industry 4.0 have progressed, networks have become larger and more complicated to manage, meanwhile network security risks also have increased; thus, like IT network management software (NMS), most OT NMS has emphasised “visibility” as the key for network management. Likewise, visibility is a major factor for network security.
Visualising OT Cybersecurity in Two Aspects
Network Security
Focus on utilising network devices to block attack behavior or virus spread. Following international standard suggestions, OT engineers can use switches and firewalls to enhance security levels. However, efficiently ensuring that large numbers of network devices are implemented correctly and are functioning well is a challenge for OT engineers, as it includes
- Checking network device deployment and identifying network cybersecurity risks
- Firewalls (firewall rules/ protocol filtering/ Industrial Protocol DPI, etc.)
- Switches & routers (port lock/ ACL/ VLAN, etc.)
- Serial-to-Ethernet converters (SSL/ SSH communication)
Network Devices Security
Focus on strengthening network devices against malicious behavior that causes networks to stop working. However, it is a challenge for OT engineers to efficiently follow security guidelines, and check and configure large numbers of network devices security settings, which include
- Changing the default password and checking password complexity
- Changing the SNMP comm. string
- Enabling trust access
- Enabling auto logout
- Enabling account login failure lockout
- etc.
Enable Visibility for OT Network Security with Moxa MXview
Ensure network security implementation
Relying on auto-scanning technology, MXview can automatically detect network device and topology and can further draw a visualised diagram to enable OT managers to see how network devices are connected with each other. OT managers can further check how firewall and switches are being implemented in their system and check if security policies are well deployed. Engineers can view VPN/ VLAN and bandwidth usage to keep the network in a good condition.
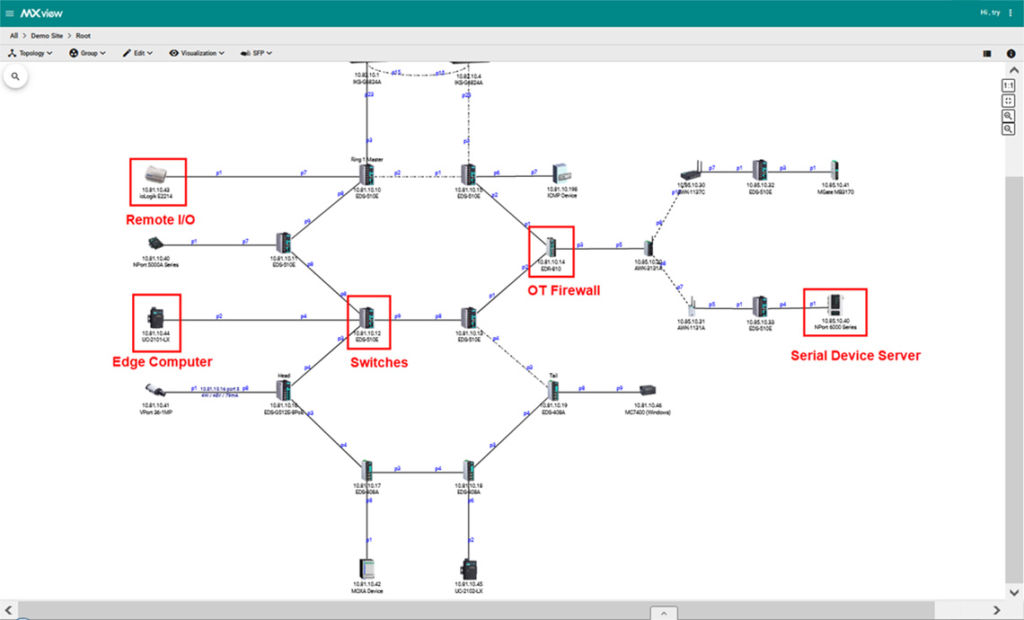
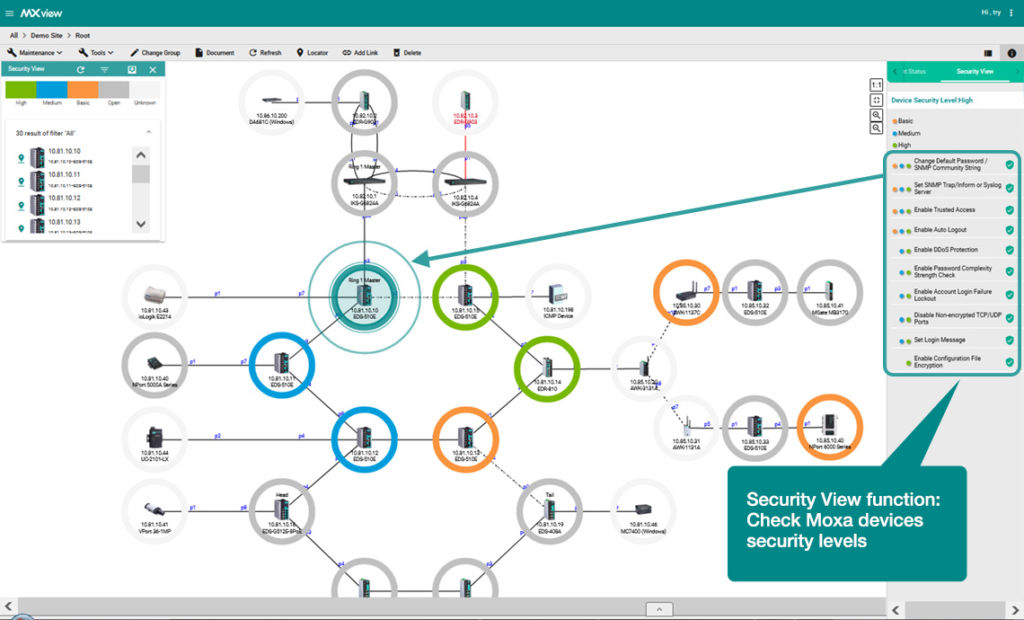
Quickly check OT device security
With the “Security View” function, OT engineers can easily check network device security levels, as it checks items that are suggested by international cybersecurity standards. With the colored identity icon, OT engineers can quickly see if any network device is not secured and take actions to configure the device to meet the security policy.
Application: Industrial Network Security Solutions for the City Water Treatment Systems
A water treatment system spanned the city and was monitorable from an industrial network. With an update plan for the next few years, the plant owner wanted to increase the network security in order to keep the infrastructure secure and meet local government regulations. However, within the city water treatment plant, there are different remote sites where water treatment systems use a large number of PLCs/ HMIs/ PCs to handle processes, which results in difficulty centrally managing and monitoring each site’s network real-time status. Moreover, there were only IT firewalls in the systems to prevent malwares from coming into the OT sites.
Considering the project manager is not an expert on network security, it was a challenge for his team to ensure that the network security was sufficient and to easily and efficiently maintain networks in the future daily operation. Due to high security concerns of city utilities, Moxa suggested that the project manager build a secured network with industrial grade EDS Series Ethernet switches, OT firewalls EDR series, and OT NMS MXview with high visibility to monitor network security and network devices security.
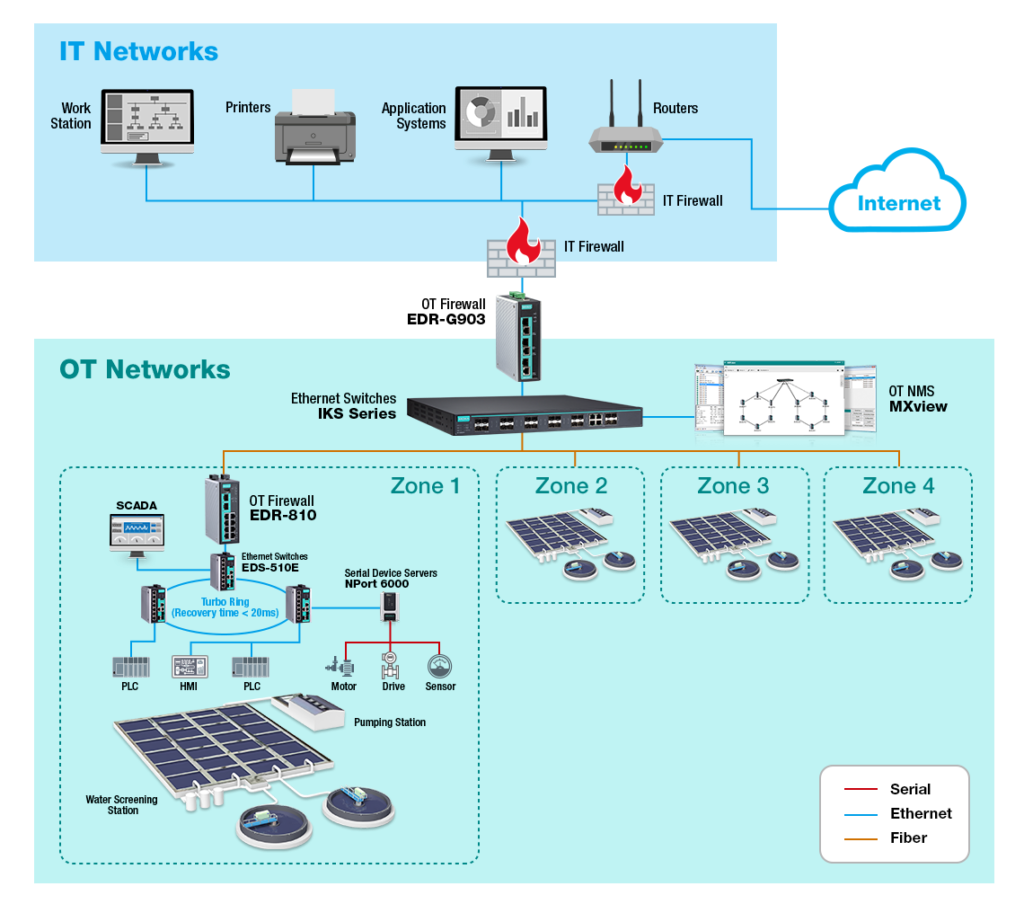
Why Moxa?
Moxa offers a wide range of network cybersecurity products for OT field sites:
- Industrial Ethernet switches compliant with the IEC 62443-4-2 level 2 security standard and with ACL function and port-lock for blocking unauthorised access based on MAC address.
- OT firewalls with industrial protocols profile & Modbus DPI
- OT firewalls policies control network traffic between different trust zones, while Network Address Translation (NAT) shields the internal LAN from unauthorised activity by outside hosts.
- MXview supports network topology scanning and Security View function. Topology scanning covers from switches and firewalls in network infra devices to serial converters in edge connectivity. Security View allows users to visualise the security status of their network so they can monitor events and perform batch configuration.
